In the world of network security, Secure Shell, commonly known as SSH, is a protocol designed to establish secure, encrypted connections over potentially insecure networks. SSH is essential for securely managing servers, transferring files, and executing commands remotely, making it a vital tool for system administrators, developers, and IT professionals. This article will explain what Secure Shell is, its uses, and a step-by-step guide to using SSH for secure connections.
Understanding Secure Shell (SSH)
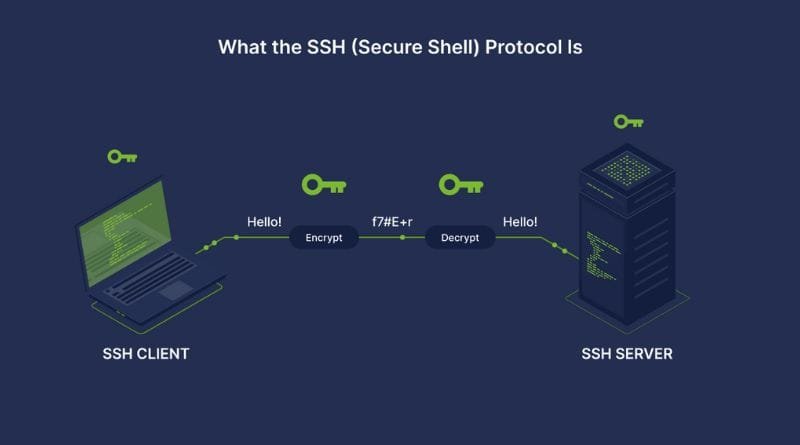
Secure Shell (SSH) is a cryptographic network protocol that enables secure communication between devices over an unsecured network, like the internet. Originally developed to replace Telnet and other insecure login protocols, SSH creates a secure channel between a client and a server. It uses public-key cryptography and symmetric encryption to ensure that data transmitted over the SSH connection remains private and secure.
SSH is commonly used for:
- Remote server management: SSH allows users to log into remote servers securely, making it essential for system administration and development.
- File transfers: SSH enables secure file transfers through protocols like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol).
- Tunneling and port forwarding: SSH can encrypt other protocols’ traffic through port forwarding, securing data transferred by applications or services that may not have built-in encryption.
Key Components of SSH
- SSH Client: The application that initiates the connection to the remote server, usually via a command line.
- SSH Server: The machine that the SSH client connects to, running SSH server software to handle incoming SSH connections.
- SSH Key Pair: SSH uses a pair of keys—a public key and a private key—for secure authentication. The public key is stored on the server, and the private key is kept on the client side. Together, these keys create a secure channel.
How to Use SSH for a Secure Connection
Step 1: Install an SSH Client
Most operating systems come with a pre-installed SSH client. Linux and macOS users can use the built-in SSH client available in the terminal. Windows users can install SSH through PowerShell or use a third-party SSH client like PuTTY. Here’s the detailed guide for windows.
Step 2: Generate an SSH Key Pair (Optional but Recommended)
Generating SSH keys is a secure way to authenticate without repeatedly entering passwords. To create an SSH key pair:
- Open your terminal.
- Enter the following command: ssh-keygen -t rsa -b 4096
- Follow the prompts to save the key files. You’ll typically save them in the .ssh folder in your home directory.
This process will create a private key (id_rsa) and a public key (id_rsa.pub).
Step 3: Upload the Public Key to the Server
If you have access to the server, upload your public key to enable key-based authentication. You can use the ssh-copy-id command: ssh-copy-id user@your-server-ip
- Replace user and your-server-ip with the correct username and server IP address.
- Alternatively, you can manually upload the key by copying the contents of id_rsa.pub to the ~/.ssh/authorized_keys file on the server.
Step 4: Initiate the SSH Connection
Once your key is set up, you can connect to the server with SSH. Use the following command to start the connection: ssh user@your-server-ip
- Replace user with your username on the server and your-server-ip with the server’s IP address.
- You should see a prompt asking if you want to continue connecting. Type yes to proceed.
Step 5: Secure File Transfers with SSH (Optional)
SSH also supports file transfers through SCP and SFTP:
- SCP: Secure Copy Protocol allows you to transfer files to and from a remote server over SSH. scp /path/to/local/file user@your-server-ip:/path/to/remote/destination
- SFTP: Secure File Transfer Protocol provides an interactive mode for secure file transfer, which can be initiated with: sftp user@your-server-ip
Tips for Using SSH Securely
- Disable Root Logins: Configure your SSH server to disallow root logins for improved security.
- Change the Default Port: By default, SSH runs on port 22, which is a common target for attacks. Changing the port number can help reduce unauthorized access attempts.
- Enable Fail2Ban: A tool like Fail2Ban monitors failed login attempts and can block IP addresses after multiple failed login attempts.
Conclusion
Secure Shell (SSH) is a powerful protocol that enables secure, encrypted communication over potentially vulnerable networks. By understanding and using SSH, you can securely manage remote servers, transfer files, and keep your data protected from unauthorized access. Mastering SSH opens a world of possibilities for anyone in system administration, web development, or IT, offering a secure, reliable foundation for remote work.
With Secure Shell, you get a highly effective way to connect securely over the internet, ensuring privacy and data integrity in an increasingly connected world.