- Introduction: Why Crypto Scams Are Rising in 2025
- 5 Top Crypto Scams to Watch Out for in 2025
2.1 Investment Scams & Pig Butchering: The Long Con
2.2 Phishing & Social Engineering Attacks: Technological Trickery
2.3 AI-Powered Deepfake Scams: The Newest Threat
2.4 Fake ICOs, Ponzi Schemes, & NFT Frauds
2.5 Wallet & Exchange Compromises - 8 Spotting Red Flags: The Crypto Scam Warning Checklist
- 5 Prevention Strategies: Protecting Your Digital Assets in 2025
- Emergency Response: What To Do If You’re Scammed
5.1 3 Immediate Actions (Within 24-48 Hours)
5.2 Reporting and Recovery (Ongoing)
5.3 Emotional and Psychological Support - Industry-Specific Advice That Works
6.1 DeFi Users
6.2 NFT Investors
6.3 Enterprises & Teams - Regulatory Landscape: What’s Changing in 2025
- Looking Ahead: New Threats and the Future of Protection
- 3 Unique, Actionable Insights for 2025
- 7 Important Practical Checklist: Protect Yourself TODAY!
- Conclusion: Stay Sharp, Stay Safe
- FAQs for Cryptocurrency and Digital Scams: 2025 Quick Answers
Introduction: Why Crypto Scams Are Rising in 2025
Cryptocurrency scams aren’t a distant threat; they are a significant and escalating risk for millions of digital asset holders. In 2024 alone, over $51 billion flowed into illicit crypto wallets, demonstrating a stunning escalation in financial crime. Today, tech-savvy criminals are leveraging advanced AI, deepfakes, and sophisticated psychological manipulation to exploit both new and seasoned participants in the digital asset space.
This comprehensive 2025 guide is designed to empower you with the knowledge and actionable steps needed to identify, prevent, and recover from cryptocurrency fraud. It combines the latest data, practical prevention strategies, real-world case studies, and reliable recovery steps, addressing critical content gaps often missed by other resources, such as the psychological impact on victims and emerging AI scam techniques.
5 Top Crypto Scams to Watch Out for in 2025
The term “crypto scam” encompasses a wide range of criminal activities, but they consistently share common tactics: trust-building, manufactured urgency, deceptive digital trickery, and emotional manipulation. Understanding these methods is the first crucial step toward real protection. Here’s how these pervasive scams work, illustrated through the real problems users face today.
1. Investment Scams & Pig Butchering: The Long Con

Investment scams promise high, guaranteed returns in volatile crypto markets, often combining persuasive social outreach with urgency and emotional appeal. The “Pig Butchering Scam” is a particularly notorious variant: a long-game fraud where scammers cultivate trust, sometimes over months, to lure victims into fake crypto investment platforms.
How It Works:
Scammers typically initiate contact through social media, dating apps, or messaging platforms, building a personal or romantic relationship with the victim. They spend weeks or months gaining trust, sharing fabricated trading successes, and gradually soliciting larger and larger investments. The victim is often allowed to make small “withdrawals” initially to build confidence, or they can “watch their money grow” on a seemingly legitimate, but entirely fake, investment platform.
Once significant funds are invested, withdrawal requests are denied with various excuses (e.g., “taxes,” “fees”), and eventually, the scammer vanishes, leaving the victim’s funds drained. This type of scam resulted in an estimated $4.4 billion in losses from pig butchering alone in 2023, with a 40% increase in scam revenue in 2024.
Example: Consider Maria, a 43-year-old who connected with “Daniel” on a travel forum. Over several weeks, their conversations became deeply personal. “Daniel” then began sharing “insider opportunities” in crypto trading, displaying fabricated screenshots of substantial returns. Maria, trusting “Daniel,” started with small investments, gradually increasing them to thousands of dollars.
The platform he directed her to allow her to “watch her money grow“. The painful truth only emerged when she attempted to withdraw her accumulated funds: her money and “Daniel” were gone.
How to Protect Yourself:
- Be Skeptical of “Guaranteed Returns”: Any promise of high, risk-free, or guaranteed profits in cryptocurrency is a major red flag. Crypto markets are inherently volatile.
- Verify Platforms Independently: Do not trust links provided by newfound online contacts. Instead, independently research any investment platform or company mentioned. Check for official registrations with financial regulators (like FINRA, SEC, or CFTC in the US).
- Beware of Emotional Manipulation: Scammers invest heavily in building trust. If an online relationship quickly moves to discussing investments, be highly suspicious.
- Test Withdrawals: If you decide to engage with a new platform, always test a small withdrawal before committing significant funds. If you can’t withdraw a tiny sum, do not invest more.
2. Phishing & Social Engineering Attacks: Technological Trickery
Phishing and social engineering attacks are primary methods for stealing wallet and exchange credentials by impersonating legitimate entities. These scams exploit human trust and digital vulnerabilities.
How It Works:
Scammers create fake emails, SMS messages, or social media posts that mimic official communications from legitimate cryptocurrency exchanges, wallet providers, or other trusted services. These messages often contain urgent warnings about security breaches or account issues, prompting users to click on malicious links. These links lead to lookalike websites designed to harvest your login credentials, private keys, or seed phrases.
Scammers may also engage in “impersonation” calls, pretending to be support representatives and using stolen personal data to gain your trust and solicit sensitive information. SMS phishing (smishing) is a common tactic where malicious links are sent directly to your phone.
Example: Imagine receiving an email that appears to be a routine security update from your cryptocurrency exchange: “Immediate action required: Security update, log in here.” The login screen looks identical to your usual portal. Hours after you enter your credentials, you discover your funds are missing from your account. This is often the result of clicking a phishing link that led to a fake website.
How to Protect Yourself:
- Verify Source, Don’t Click Directly: If a message seems urgent or “off,” do not click any links. Instead, manually navigate to the official website of the service (using a bookmark or by typing the URL directly) and log in there to check for any alerts or messages.
- Be Wary of “Support” Requests: No legitimate service will ever ask for your private key, seed phrase, or full control of your wallet. Be suspicious of any “support agent” asking for sensitive information over email, phone, or chat.
- Enable Strong Two-Factor Authentication (2FA): Always use an authenticator app (like Google Authenticator or Authy), not SMS, for 2FA on all your crypto accounts. SMS-based 2FA is vulnerable to SIM-swapping attacks.
- Check URLs Carefully: Before entering any information, double-check the URL in your browser’s address bar for subtle misspellings or extra characters.
- Avoid Sharing Device Screens Remotely: Never allow unknown persons to access your device via remote desktop or screen-sharing applications.
3. AI-Powered Deepfake Scams: The Newest Threat
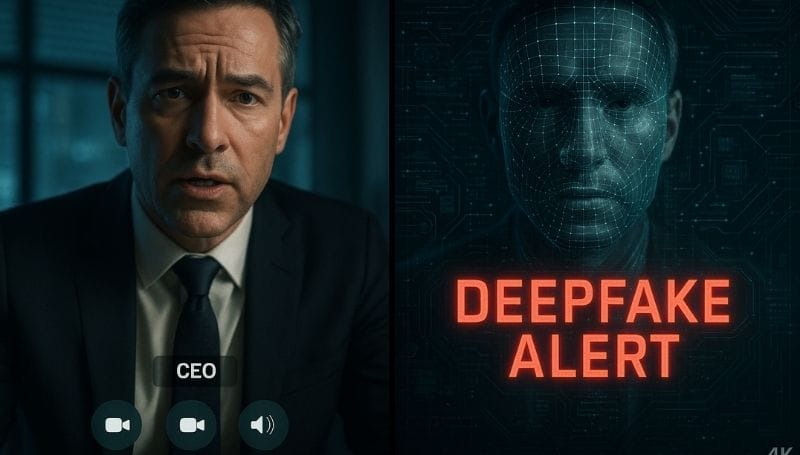
A rapidly emerging threat in 2025, AI-powered deepfake scams use artificial intelligence to fabricate synthetic videos, audio, or chatbots that convincingly imitate real people.
How It Works:
Criminals leverage AI to generate highly realistic audio and video that can bypass traditional verification methods. They might impersonate celebrities, well-known CEOs, or even victims’ relatives to solicit funds or trick users into revealing wallet credentials.
These scams are becoming more sophisticated and convincing, making them incredibly difficult to detect without careful scrutiny. Documented cases of AI-powered deepfake scams have already collected over $5 million.
Example: A mid-sized crypto startup experienced this first-hand when their CFO received a panicked voice call from her “CEO”. The voice perfectly matched her CEO’s, and the caller ID appeared legitimate. The “CEO” urgently requested a cryptocurrency transfer to “secure a market opportunity”. By the time suspicion arose, $120,000 had been wired to a scammer using highly convincing deepfake audio.
How to Protect Yourself:
- Double-Check with Non-Digital Channels: If you receive an urgent or unusual request from a seemingly familiar person, especially involving money transfers, always confirm through a different, non-digital channel (e.g., a direct phone call to a known number, or meeting in person).
- Be Skeptical of Unsolicited Videos/Audio: Never automatically trust videos, voice messages, or social media “screenshots” in 2025, as AI makes “proof” highly suspect.
- Educate Employees and Family: Ensure that individuals, especially those handling finances, are aware of deepfake tactics and are trained to verify identities independently.
4. Fake ICOs, Ponzi Schemes, & NFT Frauds

These scams revolve around creating fraudulent investment opportunities or digital assets that appear legitimate but are designed to “exit-scam” or collapse once sufficient funds are raised.
How It Works:
- Fake ICOs (Initial Coin Offerings) and Ponzi Schemes: Scammers launch new tokens or projects with elaborate whitepapers, detailed roadmaps, and impressive-looking (but fake) team bios. They generate significant hype on social media and forums, encouraging investment. In Ponzi schemes, early investors are paid with funds from newer investors, creating an illusion of profitability until the scheme inevitably collapses. For ICOs, once enough funds are raised, the “founders” vanish, leaving investors with worthless tokens.
- NFT Frauds: These include phishing attacks targeting NFT marketplaces, “rug pulls” where creators abandon a project after selling NFTs, or the sale of forged, non-original, or malicious NFT collections. Scammers might create lookalike NFT collections or marketplace landing pages.
Example: Consider a highly hyped new NFT project launched on social media, promising guaranteed resale profits. The excitement leads to a buying frenzy. However, the day after the public sale, the “founders” disappear, leaving buyers with unusable image files and empty wallets. This is a common “rug pull” scenario in the NFT space.
How to Protect Yourself:
- Thorough Due Diligence: Research the team, roadmap, and whitepaper of any crypto project. Legitimate projects have transparent teams and publish detailed, achievable goals.
- Check Code and Community: For new tokens or DeFi projects, check if their code is publicly available on platforms like GitHub. Engage in reputable online communities (e.g., Reddit, Bitcointalk) to check for prior scam warnings or discussions about the project’s legitimacy.
- Validate Smart Contract Addresses for NFTs: Before purchasing an NFT, always verify the smart contract address directly on a block explorer (like Etherscan or Solscan) to ensure it belongs to the legitimate collection, not a fake one.
- Avoid FOMO (Fear of Missing Out): Scammers often create intense urgency to push rushed purchases. Take your time, do your research, and don’t succumb to pressure.
- Demand Audits for DeFi: Only interact with DeFi applications that have prominent, independent security audits from credible cybersecurity firms.
5. Wallet & Exchange Compromises

These scams directly target the security of your cryptocurrency wallets and exchange accounts, often through sophisticated hacking techniques or by exploiting vulnerabilities.
How It Works: Attackers can gain access to your assets through various means:
- Phishing for Exchange Credentials: As mentioned, this is a primary method for stealing login details.
- SIM Swapping: Criminals gain control of your phone number by tricking your mobile carrier, then use this to bypass two-factor authentication (if it’s SMS-based) and access your accounts.
- Malicious Wallet Apps: Scammers disguise harmful software as legitimate wallet applications. Once downloaded and used, these apps can drain your holdings upon login.
- Exploiting Exchange or Smart Contract Vulnerabilities: Even legitimate platforms can have security flaws. Hackers exploit these vulnerabilities to steal funds directly from exchanges or decentralized finance (DeFi) protocols.
Example: A popular DeFi platform, trusted by many due to its popularity, recently suffered a “flash-loan attack,” resulting in dozens of users losing their funds overnight. Most victims had relied solely on the platform’s reputation, not its underlying security audits, highlighting that even experienced users can be caught off guard.
How to Protect Yourself:
- Select Non-Custodial Wallets: For storing significant amounts of cryptocurrency, prioritize hardware wallets (e.g., Ledger, Trezor) over software wallets or exchange accounts. Hardware wallets keep your private keys offline, making them much harder to compromise.
- Master Private Key Protection: Your private key or seed phrase is the master key to your funds. Never store it digitally (e.g., on your computer, phone, or in cloud storage) and certainly never share it with anyone. Write it down and store it in a secure, physical location.
- Use Authenticator Apps for 2FA: Reiterate: Always use an authenticator app for 2FA, not SMS.
- Only Use Regulated Exchanges: Stick to exchanges that are registered with relevant financial regulators in your jurisdiction. These platforms often have better security standards and legal recourse in case of issues.
- Beware of Copycat Sites: Always double-check URLs and bookmark official portals to avoid accidentally landing on a fake website.
- Stay Updated: Regularly install security updates and app patches for your wallets, operating systems, and other software.
8 Spotting Red Flags: The Crypto Scam Warning Checklist
Recognizing scam tactics is crucial. Here’s a simple, no-nonsense checklist to help you spot almost any scam:
- Too-Good-To-Be-True: Promises of guaranteed profits or risk-free investment opportunities. In volatile, real-world crypto markets, “no risk, high reward” claims are always false.
- High Pressure: Insistent urgency, such as “invest today, offer ends tomorrow” or “act now, before it’s too late”.
- Withdrawals Blocked: Sudden new “taxes,” unexpected fees, or excuses for not returning funds when you try to withdraw. The blockchain is borderless, so delays are almost always a sign of fraud.
- Unlicensed Platforms: The platform has no registration with regulators, few or no credible reviews, or sparse team information.
- Requests for Secrets: Anyone who asks for your private key, seed phrase, or demands full control of your wallet. No legitimate service will ever ask for these.
- Fake Proof: Doctored screenshots of fake profits, testimonials from paid actors, or impersonated celebrities.
- Suspicious Communication: Misspelled URLs, fake websites, or cryptocurrency projects that lack publicly identifiable founders or developers.
- Promises of “Recovery” for an Upfront Fee: Many “recovery services” are secondary scams designed to defraud victims again.
| Pro tip: Use Google Lens or reverse image search on any photos provided by online contacts. Scammers frequently reuse photos and testimonials stolen from real people. |
5 Prevention Strategies: Protecting Your Digital Assets in 2025

Most crypto scams can be stopped with practical, consistent countermeasures. Proactive defense is your best asset.
1. Lock Down Your Wallet
- Use a Hardware Wallet: For any significant holdings, invest in a hardware wallet (e.g., Ledger, Trezor) and store your assets offline.
- Private Key Golden Rule: Your seed phrase is the master key. Never share it, store it digitally, or give remote access to your device to anyone, even “support”.
- Two-Factor Authentication (2FA): Always enable 2FA using an authenticator app (like Authy or Google Authenticator), not SMS, for all your cryptocurrency exchange and wallet logins.
- Stay Updated: Promptly install security updates and app patches for your wallet software and operating systems.
2. Vet All Platforms and Offers
- Search for Official Registration: Before investing, check if a platform is registered with relevant financial regulators (e.g., FINRA, SEC, CFTC for US users). If there’s no registration, walk away.
- Check Community Reviews: Actively look for discussions and warnings on reputable forums like Reddit, Bitcointalk, or trusted Discord communities. Scam alerts spread quickly within informed communities.
- Demand Audits: For decentralized finance (DeFi) projects, insist on prominent, independent security audit reports from credible cybersecurity firms. No audit means no trust.
3. Practice Safe Communication
- Email & Social Media Smarts: If a message, email, or social media post looks urgent or “off,” do not click any links or reply. Instead, contact the official website or support directly through verified channels.
- No Screensharing: Never permit unknown individuals remote access to your device via desktop sharing or screen mirroring tools. This is a common tactic for scammers.
- Validate Contact Requests: Always confirm the identity of anyone requesting you to move funds or provide sensitive information, especially if the request comes via an unexpected channel.
4. Test Investment Opportunities
- Before sending real money: If you are considering a new investment platform, always test a small withdrawal (e.g., $1–$10) first to confirm functionality before committing larger sums.
- Ask Direct Questions: Inquire about licensing, team details, and the underlying technology, then independently verify all claims.
- Search for Warnings: Proactively search “[platform name] scam” or “[platform name] reviews” to see if any complaints or red flags have been raised by others.
5. Build Your Knowledge Base
- Subscribe to Official Alerts: Sign up for scam alert feeds and consumer guidance from authorities like the FBI, IC3, U.S. Securities and Exchange Commission (SEC), or Commodity Futures Trading Commission (CFTC) in your jurisdiction.
- Educate Yourself and Others: Continuous awareness training is crucial, especially for vulnerable groups like seniors. Americans over 60 lost an estimated $2.8 billion to crypto scams last year. Share best practices with family and friends.
Emergency Response: What To Do If You’re Scammed

If you unfortunately fall victim to a crypto scam, immediate and decisive action can make all the difference. Success rates for recovery drop dramatically the longer funds are gone. Here’s a practical, step-by-step process:
3 Immediate Actions (Within 24-48 Hours)
- Stop All Transactions, NOW:
- Do not send any further funds to the scammer, even if they promise to return your initial investment or claim to be a “recovery agent”.
- Block all communication from the scammer immediately.
- Be highly suspicious of any “recovery service” that contacts you, as this is likely another scam (double victimization).
- Document Everything:
- Save all communications: Take screenshots of every text, email, chat message, social media interaction, and any platform URLs used by the scammer.
- Record all transaction IDs/hashes: Note down all wallet addresses involved, the exact amounts sent, and the dates and times of transactions.
- Gather all platform details: Collect account names, usernames, and any other relevant identification.
- Secure Your Remaining Assets:
- If any funds remain in compromised wallets or exchange accounts, transfer them immediately to fresh, secure, and uncompromised wallets (preferably a hardware wallet).
- Change passwords for all related accounts (exchanges, email, social media) that might have been compromised or linked to the scam.
Reporting and Recovery (Ongoing)
- Report to the FBI IC3: File a clear, detailed report with the FBI Internet Crime Complaint Center (IC3). Provide all collected transaction data, evidence, and contact information. Filing a complaint creates an official record and helps authorities track criminal groups.
- Contact SEC and CFTC: For scam investment opportunities, use the online complaint portals of the U.S. Securities and Exchange Commission (SEC) and the Commodity Futures Trading Commission (CFTC).
- Notify Relevant Platforms: Contact the support team of your cryptocurrency exchange or wallet provider immediately. Provide them with all evidence, including transaction IDs, and request urgent freezes of any affected accounts or funds, if possible.
- Legal Recovery Options and Realistic Expectations: While successful asset recovery rates remain low (globally, only about 15% of funds are recovered), rapid reporting and engagement with law enforcement and exchanges may increase the odds. Seek specialized attorneys in cryptocurrency fraud. Many major cities now have crypto law practices. Be prepared for long, complex processes with realistic expectations.
- Avoid “Recovery” Scams: Be vigilant against individuals or services that promise to recover your funds for an upfront fee. These are almost always secondary scams designed to defraud you again.
Emotional and Psychological Support
Victim Support: Falling victim to a scam can be emotionally devastating. Shame and isolation are common feelings, but they are unwarranted. Connect with online support groups (e.g., Reddit’s r/cryptoscams), victim helplines (like The Cyber Helpline), or local cybersecurity nonprofits to process the emotional fallout. Recovery isn’t just about money; it’s also about psychological well-being.
Industry-Specific Advice That Works
Tailored strategies are crucial for different segments of the crypto ecosystem.
DeFi Users
- Always use audited platforms: Before interacting with any decentralized finance (DeFi) protocol, check for prominent, independent security audits on platforms like CertiK or DeFiSafety.
- Understand Smart Contract Risks: Anyone can deploy a DeFi contract. Don’t trust a protocol based solely on popularity; understand that vulnerabilities can lead to significant losses.
- Spread Risk: Never keep all your assets in a single DeFi protocol or wallet. Diversify your holdings to mitigate risk.
NFT Investors
- Check Contract Addresses: Before purchasing an NFT, always verify the smart contract address directly in your wallet or browser extension using block explorers (e.g., Etherscan, Solscan).
- Watch for Fake Listings and Phishing: Be highly vigilant for lookalike NFT collections or marketplace landing pages designed to steal your credentials.
- Avoid FOMO (Fear of Missing Out): Rushed purchases driven by hype are the most vulnerable to scams. Take your time and verify.
- Regularly Transfer Valuables: Move high-value NFTs from hot wallets (used for daily transactions) to a secure cold wallet.
Enterprises & Teams
- Employee Training: Implement regular phishing drills and wallet safety education for all staff. This is critical for defending against sophisticated social engineering and deepfake attacks.
- Multi-Signature Wallets: For all treasury and payroll actions, mandate the use of multi-signature (multi-sig) wallets, which require approval from multiple parties for large transfers.
- Formalize Incident Response: Develop a detailed crypto-incident plan with legal, compliance, and fintech consultants, outlining clear steps to take if digital theft occurs.
Regulatory Landscape: What’s Changing in 2025
The period of 2024-2025 has seen significant regulatory action and increased law enforcement response to cryptocurrency crime.
- Increased KYC/AML on More Platforms: New regulations mean that most centralized cryptocurrency services now require stringent identity verification (Know Your Customer/KYC) and anti-money laundering (AML) checks.
- Global Law Enforcement Collaboration: Cybercrime knows no borders. Law enforcement agencies in the US (FBI, DOJ), EU (Europol), and Asia are now partnering on arrests, asset freezes, and information sharing to combat transnational crypto criminal organizations.
- Liability and Recovery May Improve: Some jurisdictions are starting to implement rules that compel platforms to help trace and freeze illicit assets. While this is a positive development, time remains critical for successful intervention.
What This Means for You: Using services that comply with your country’s regulations generally increases your chances of recovering funds or receiving support if a scam occurs. Compliance with reporting procedures, such as through the FBI’s IC3 portal, and thorough information documentation significantly improve the chances of broader legal action and potential recovery.
Looking Ahead: New Threats and the Future of Protection

The cryptocurrency security landscape is constantly evolving. Staying informed about future trends is essential for ongoing protection.
- Sophisticated AI: Expect even more realistic impersonations in AI-generated video, voice, and written communications used in targeted scams. Threat actors will use AI to generate highly convincing synthetic media that can bypass traditional verification methods.
- Targeted Social Engineering: Scammers will increasingly leverage personal data, often scraped or purchased from data breaches, to craft highly personalized and effective social engineering attacks.
- Evolving DeFi and NFT Targeting: As more value moves on-chain, rug pulls, flash loan attacks, and NFT forgeries are expected to grow in frequency and sophistication.
- Regulatory Uncertainty: Global disparity in cryptocurrency regulation continues to create loopholes that criminals exploit. While enforcement is strong in the US and EU, new jurisdictions (especially in Asia) are evolving rapidly.
- Emerging Protections: New preventive solutions are on the horizon, including AI-based fraud detection systems, advanced multi-chain analytics for tracing illicit funds, biometric verification methods, and potentially mandatory insurance requirements for exchanges and wallets. Users must stay vigilant and adapt to new technologies as they emerge.
3 Unique, Actionable Insights for 2025
Beyond the technical safeguards, a fundamental shift in perspective can offer unique protection in 2025:
- Scams Are Relationships: Unlike old-school phishers, many crypto scammers today build ongoing trust and personal relationships before stealing. The longer the “relationship” they cultivate, the larger the potential loss. Be acutely aware of this pattern in any new digital or financial interactions, particularly those that quickly become emotionally charged.
- AI Makes “Proof” Suspect: In 2025, never implicitly trust videos, voice messages, or social media “screenshots” without double-checking through entirely separate and confirmed channels. AI’s ability to create convincing fakes means traditional forms of digital “proof” are no longer reliable.
- Lost Money Isn’t the End: If you are scammed, remember that documenting your experience and reporting it to authorities can not only help warn thousands of potential future victims but may also serve as your legal bridge to recovery if criminals are eventually caught and assets seized. Your experience can contribute to collective defense.
7 Important Practical Checklist: Protect Yourself TODAY!
Here’s your essential, actionable checklist to enhance your crypto security right now:
- Hardware Wallet: Use a hardware wallet for storing any significant amounts of cryptocurrency.
- 2FA (Authenticator App): Enable Two-Factor Authentication (2FA) on every crypto account, using an authenticator app (e.g., Google Authenticator, Authy), not SMS.
Learn More: Data Privacy in the Digital Age: Tips for Protecting Your Personal Information
- Ignore “Guaranteed” Returns: Be deeply skeptical of any promise of guaranteed crypto profits or risk-free investment opportunities.
- Test New Platforms: Before committing significant funds, test any new platform by attempting a small withdrawal (e.g., $1–$10).
- Document & Report: If you suspect or confirm a scam, document everything (screenshots, transaction IDs), then report immediately to authorities (FBI IC3, SEC/CFTC), and move any remaining funds to a secure wallet.
- Stay Updated: Subscribe to official scam alerts from organizations like the FBI, SEC, or CFTC in your jurisdiction.
- If in doubt? STOP: If something feels “off” or too good to be true, stop all actions and verify with trusted, independent sources first.
Conclusion: Stay Sharp, Stay Safe
The scale and sophistication of cryptocurrency and digital asset scams in 2025 underscore the critical need for continuous awareness, practical prevention, and transparent recovery resources. Digital asset freedom comes with new risks—and new responsibilities.
The best protection in 2025 is a combination of vigilance, clear-eyed skepticism, and a readiness to act fast if something goes wrong. By understanding modern scam tactics, rigorously verifying platforms and opportunities, practicing robust self-defense, and acting quickly in the event of a loss, digital asset holders can substantially reduce their exposure and potential damages.
Remember:
- Don’t go it alone: Utilize trusted communities, official authorities, and support networks for advice and backup.
- Education is your edge: Share your knowledge with those around you, especially newcomers, to strengthen the entire crypto ecosystem against evolving threats.
- Scams may evolve, but your core defense—clarity, caution, and community—will always be your most powerful tool.
Stay secure, question everything, and don’t let fear keep you from the real opportunities blockchain technology brings. Empower yourself, and you empower the future of finance.
FAQs for Cryptocurrency and Digital Scams: 2025 Quick Answers
Here are quick, direct answers to common questions about crypto scams in 2025, optimized for clarity and featured snippets:
- What are the most common types of cryptocurrency scams in 2025?
Investment scams (especially pig butchering), phishing, deepfake requests, fake ICOs, Ponzi schemes, and NFT market schemes.
- How much money was lost to crypto scams in 2024?
Over $51 billion flowed into illicit crypto wallets globally. Specifically, $5.8 billion was lost to investment scams in the US alone, with $2.8 billion lost by American seniors.
- What is pig butchering and how does it work?
It’s a long-term scam where fraudsters build fake romantic or mentorship relationships online, convince victims to invest in fraudulent crypto platforms, and gradually drain the victim’s assets over weeks or months.
- How can I protect my cryptocurrency from scams?
Use hardware wallets for large holdings, enable strong multi-factor authentication (MFA) via authenticator apps (not SMS), never share private keys or seed phrases, verify exchanges and platforms independently, and perform thorough research before investing.
- What should I do if I’ve been scammed with cryptocurrency?
Immediately stop further transfers, document everything (screenshots, transaction IDs), report to authorities (FBI IC3, SEC, CFTC), and seek legal counsel or victim support groups.
- How do I report cryptocurrency fraud to authorities?
File a complaint with the FBI Internet Crime Complaint Center (IC3), and report investment fraud to the SEC or CFTC using their online forms.
- Can stolen cryptocurrency be recovered?
Recovery rates remain low (globally, only about 15% of funds are recovered), but rapid reporting to authorities and exchanges, along with comprehensive documentation, may increase the odds. Prevention is significantly more effective than recovery.
- What are the warning signs of a crypto investment scam?
Guaranteed high returns, pressure to invest quickly, requests for private keys or seed phrases, inability to withdraw funds, and fake social proof (e.g., doctored screenshots, celebrity endorsements).
- How are AI and deepfakes being used in crypto scams?
Attackers create synthetic audio, video, or text mimicking real people or authorities to trick victims into sending money or revealing sensitive information. This makes “proof” highly suspect.
- Why do seniors lose more money to crypto scams?
Seniors are often targeted due to financial vulnerability, potentially lower digital literacy, and a higher trust in traditional relationship-building approaches that scammers exploit.